Most crypto exchanges allow users to access their accounts using API keys as an alternative to password/2FA-based authentication. While API keys open the door to data analysis, trading bots, and other automations, crypto traders may not be fully aware of the risks associated with sharing API credentials with non-trustworthy third parties.
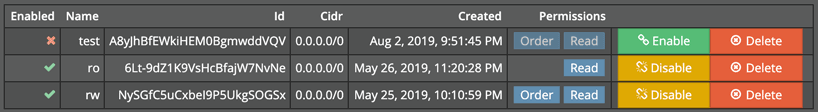
API key management on BitMEX
Some presume that as long as fund withdrawal privilege isn’t granted, it’s safe to give out trading API keys to third party websites or apps. They can’t possibly steal coins out of your pocket, right?
Wrong. One way to siphon money off your account with API keys is through a pump-and-dump scheme. An attacker first identifies a relatively illiquid coin (e.g. XYZ with a XYZ/BTC trading pair). After building a long position in XYZ in their own account, they abuse victims’s trading API keys to convert altcoins to Bitcoin if necessary, place a large number of XYZ market buy orders in quick succession to inflate its price, and dump their own holdings to the market to realize gains in Bitcoin. The process may be repeated to drain compromised accounts.
All of the account balance can’t be captured by the attackers – part of it goes to other traders and to the exchange via transaction fees, but if the chosen asset is obscure and normally trades at a low volume, it costs little to clear the orderbook and mount a profitable attack. This is not just a theoretical possibility; it actually happened to dozens of Binance users and the VIA/BTC trading pair in March 2018.
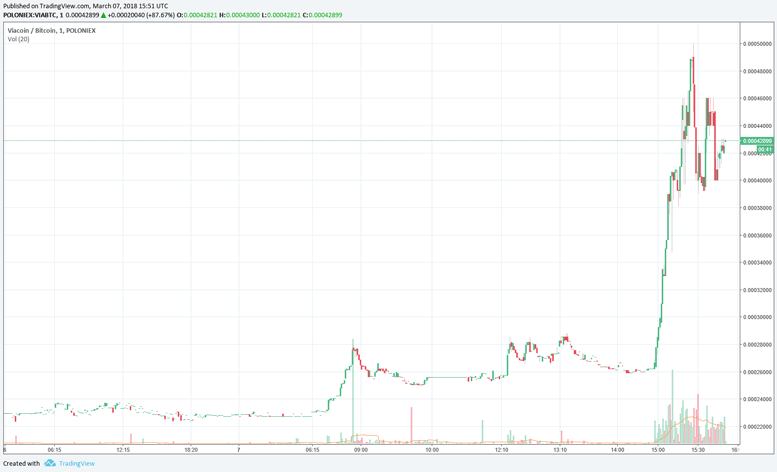
Binance VIA pump in March 2018
A less traceable heist might involve opening a large altcoin/XBT position in a futures market at high leverage and manipulating the price of the underlying asset in a spot market with compromised API keys.
One might think that sharing a read-only API key with third-parties such as https://pnl.bitwise.cc would be safe because they can neither withdraw nor trade on your behalf.
A read-only API key can’t wreak much havoc indeed, yet it could be abused by a malicious party. For example, BitMEX’s read-only API key lacks fine-grained level of control. It allows a user to spy on your trading strategy by reading order execution history, even though they may claim to be checking your margin status only. It even allows a user to send chat messages to the trollbox which is hardly justifiable as a read operation.
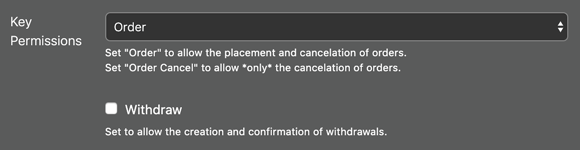
Coarse-grained API key permission settings on BitMEX
https://pnl.bitwise.cc does NOT abuse users’s API keys (trust us!), but you really have no way to verify this claim. Even if the website were open-sourced, you get no guarantee that the server is running a binary compiled from the same codebase. For the same reason, you should think twice about handing over API keys to third party mobile apps even if they have a seemingly legit open source repository.
Again, bitwise.cc does not abuse API keys. Hundreds of users have trusted us, and so should you. But we’d rather earn your trust by presenting you with verifiable proofs than hollowly repeating “trust us”. The Russian proverb “Trust, but verify." is not good enough when it comes to crypto; what we should subscribe to is “Verify, then trust." That, my friend, is the spirit of crypto-currency.
Having mulled over the trust issue in handling API keys, we’ve come up with a practical solution for secure API trading. Our method trades off some convenience and usability for a high level of privacy and security. We assure you that API secrets won’t ever leave your local computer. Of course, don’t take our word for it.
Verify, then trust.